What is a Clickjacking Attack?
Table of Contents
- By Greg Brown
- Published: Feb 06, 2023
- Last Updated: Feb 09, 2023
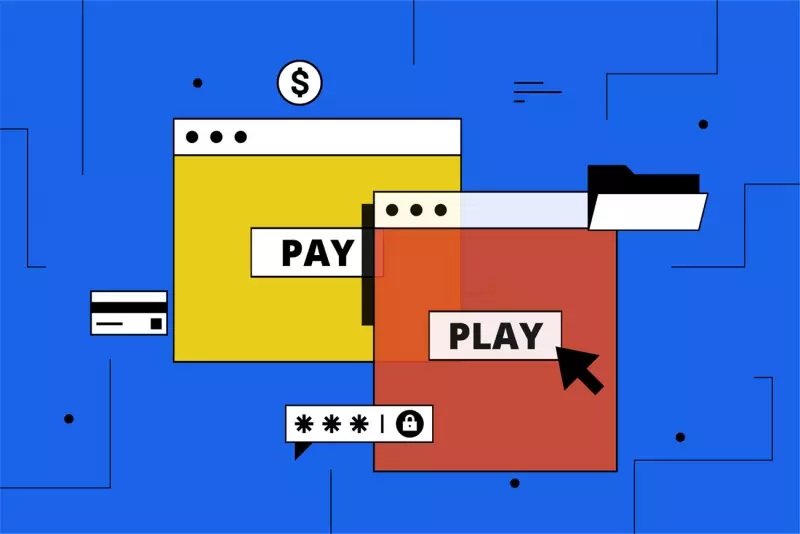
Have you ever been online, and clicked on an interesting link only to be taken to an unfamiliar website? Clickjacking (or UI redress) attacks trick users into clicking on an element in a genuine webpage and, instead, taking to a clickjacking site.
Unethical ad agencies use this technique to bolster click rates for poorly performing web pages. Predators use the technique to download malware, obtain sensitive or private credentials, and transfer money.
Clickjacking
Clickjacking is not an easy hack for new or inexperienced predators. The process is made possible by HTML frames. Before HTML5, graphical browsers used a collection of frames inserted into an HTML document. iFrames are essentially a frame within a frame. An example. when you visit a webpage with an embedded YouTube video. The video exists within an iFrame.
Clickjacking starts when an attacker covers the original page with a transparent JavaScript or UI elements layer. The outward appearance of the clickjacked page appears unchanged, which gives users no reason to question whether an attack is happening.
Users navigate a page as they usually would without realizing the clickjacking is underway. Users continue to browse the page as if nothing is wrong, links and buttons work as they should.
Clickjacking Attacks can take on many forms:
- Malware download
- Steal banking credentials
- Activate webcams
- Location tracking
- Boosting ad revenues
Unwitting users can be led to believe they are typing in banking and financial credentials into a legitimate website, when they are handing them over to predators.
Scams such as clickjacking usually involve some form of social engineering to get users to the site. Using social media to manipulate a person’s behavior is built around how people act and think, making it a perfect vehicle for a clickjacking attack.
Predators do their best to understand what motivates a person. Once this motivation is determined, predators easily deceive their victims. Also, scammers count on unwitting employees and individuals to carry out malicious threats.
Clickjacking is not just about mouse clicks. With a combination of CSS, text boxes, and iframes, predators can trick their victims into giving up every piece of personal information.
Variations of Clickjacking Attacks
Clickjacking is a lucrative attack for predators who know HTML. The malicious action, such as stealing login credentials, cannot be traced back to the attacker because the victim was legitimately logged into their account.
LikeJacking
Likejacking is the same as clickjacking, only with a more specific purpose. This scam is carried out through Facebook and tricks the user into Liking a specific page using the “LIKE” button. Many will question the purpose of high-jacking a like button. However, when big advertising dollars are at stake, most people do anything to accomplish their goals.
Cursorjacking
Cursorjacking attacks occur when a predator replaces the actual cursor with an image. The user perceives their cursor is in one position when it is actually on some other page element clicking an advertisement. Victims believe they click on a valid element when they click a malware download button. The actual cursor may remain visible on the page hidden away; however, predators want you to concentrate on the fake cursor.
Cookiejacking
This form of clickjacking is one of the more complicated attacks. The victim is tricked into dragging and dropping an element on a page, such as a video. They are actually selecting the contents of a cookie on an invisible page. Once the attacker has been given all the contents of a user’s cookies, they can perform any action on a target website.
Filejacking
Users who upload and transfer photos to social media or another user are ripe for this attack. When you wish to upload photos, a window opens which says, “Browse Files” Actually, a predator’s active file server has been opened, giving the predator full access to every file on your computer.
Prevent Clickjacking Attacks
Unfortunately, there is never a perfect defense against malware, phishing, and clickjacking attacks. However, as defensive technology becomes more complex, the aftermath of an attack can be lessened and eventually mitigated.
There are generally two ways to defend yourself against clickjacking attacks.
- Client-side Methods; this type of defense can be suitable in some instances; however, client-side defense is easily bypassed. The most common client-side defense is frame-busting.
- Server-side defense; most security experts advise using a server-side method against clickjacking. X-frame options are the most effective means against attacks.
Anti-Clickjacking browser extensions: every major browser has developed preventative apps against clickjacking. However, the problem becomes, the extension disables all JavaScript code. This does not lead to the optimal user experience. Some extensions have an allow list where the user can permit downloads.
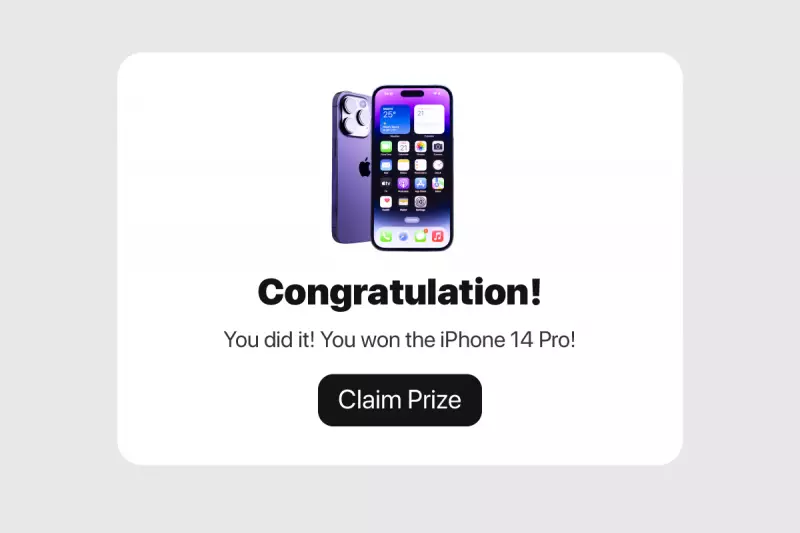
Never click on an ad that is just too good to be true—clicking on these ads will more than likely take you directly to a clickjacking website. Look for news on reputable sites with a history of secure information delivery.
Never download anything from an email or website that looks suspicious. The single biggest advantage scammers have; unwitting users or employees. Clickjacking websites provide plenty of false layers for a user to log into. Stay vigilant and only download apps from reputable app stores or repositories.
Be on the lookout for emails that claim to address an urgent matter for the user. These suspicious emails are likely from medical, financial, or government sites. The urgent matter will always require users to click on a link and then be taken to a site that may look exactly like the website you expect to see, such as your doctor’s website or your bank.
Final Word
Clickjacking and other forms of cyberattack are not going away any time soon. Unfortunately, predators find new and complex ways to steal money and information from unwitting people. The only way to protect yourself is awareness of your surroundings; take the necessary steps to protect your information.
New secure ways of building websites and transferring money are always in development, such as the X-frame header. As mentioned earlier, a predator’s greatest advantage is an unwitting user who thinks clickjacking can never happen to them.
















