What is Cyberbullying and How to Stop it
Table of Contents
- By Rita
- Published: Apr 01, 2022
- Last Updated: Nov 23, 2023
The internet is an excellent medium for users to connect with people. It promotes global communication. However, it also harbors the risk of cyberbullying. It is important to know how to prevent cyberbullying, especially if you are a parent.
Cyberbullying
Cyberbullying often transpires within the teenage community. Here are some cyberbullying facts you probably didn’t know. Sadly, 37% of teenagers between the ages of 12 and 17 are bullied online. In addition, 60% of this community have witnessed this online harassment without intervening.
Many believe cyberbullying takes place privately. But, most of it occurs publicly. Instagram holds the highest rate of cyberbullying. A whopping 42% of its users have reported harassment on the app. Online bullying also takes place on various other social media. These include Facebook, Twitter, gaming platforms, and even online schooling websites.

What is Cyberbullying Exactly?
Cyberbullying is the act of repeatedly harassing an individual through electronic devices. This form of bullying is a much more complex issue to identify than traditional bullying.
With traditional bullying, it’s easy to spot when bullies are ganging up on a victim. Signs like bruising are a dead give-away. Unfortunately, cyberbullying hides behind privacy, anonymity, and discretion, so bullies get away with it a lot more.
Still, it is no less harmful than traditional bullying. This form of bullying doesn’t involve physically harming another individual. However, it may still cause tremendous psychological damage.
Cyberbullying is especially harmful because most information on the internet is permanent. For example, the bully might post hurtful rumors, videos, or pictures on social media for everyone to see. These viewers may comment on their own opinions or share the information, which will cause harm to the victim.
Can Cyberbullying Happen to Adults?
Most instances of cyberbullying on the news come from school-age children. However, today’s adults are equally reliant on the internet for communication, which also opens them up to cyberbullying.
Older users are also better at hiding their identity online and don’t have a direct authority figure to answer to. This combination can be deadly and could lead to far more calculated and dangerous methods for attacking others online.
Adult cyberbullying cases can destroy the victim’s mental health, but adults have other things to lose. It can destroy careers and relationships as well. Because adults are harder to hold accountable, it’s even more critical for bystanders to take action in these cases.
What is a “Bystander” in Cyberbullying?
Bystanders are an essential part of the bullying dynamic. They are the people watching an instance of bullying who have the choice of doing nothing or acting against the attacker. In a sense, it’s the bystanders that dictate what is socially acceptable.
In the context of cyberbullying, bystanders are the other people in the comment section or chat where the attack occurs. In some ways, it’s even more challenging for a bystander to act against cyberbullying than traditional bullying.
It’s not the same as seeing a bully at school and telling a teacher. There’s no readily available authority on the internet to which they can report the instigator. Their only option is often to call out or confront the bully.
Standing against cyberbullying is the obvious choice. But there are many reasons a bystander may not step in to save the day.
- They’re afraid that others won’t back them up.
- They do not know the victim.
- They don’t know the entire situation.
- They don’t believe anything will change if they step in.
- They worry the bully may turn on them, and they may become the next victim.
A stressful situation can prevent people from thinking rationally, especially teens and young adults. However, studies show that nearly half of cyberbullying cases can be prevented through bystander intervention. This has prompted many social media sites to start nudging people into action.

Types of Cyberbullying
Before you can work on preventing cyberbullying, you need to understand the different types of cyberbullying. This will help you recognize which factors to look for when advocating against bullying.
- Harassment - Continuously sending unwanted, offensive, or hurtful messages to an individual. This is known as text-based harassment.
- Exclusion - Purposefully excluding someone to hurt their feelings or make them feel like an outcast.
- Trickery - This involves tricking someone into revealing private or embarrassing information. The bully will then share this information online.
- Fraping – Stealing the victim’s social media account and using it to post harmful or destructive content while pretending to be the victim. This is an attack on the victim’s reputation.
- Outing - This is when an individual willfully shares private information about someone on a digital platform. It is usually done to harm or embarrass that person.
- Cyberstalking - is The act of harassing someone by repeatedly sending insults and threats. A severe subcategory of this is online sexual harassment. It includes frequent threats of assault. The individual may even receive unwanted sexually explicit images and texts.
- Dissing - This is when one spreads false rumors about someone to ruin their reputation and friendships.
- Trolling – Intentionally posting untrue or provocative information online to upset the victim. This is often done in the hopes that the angry party will respond with something equally toxic and embarrass themselves.
Cyberbullying and Social Media
Social media is only growing, and more of our interactions are being relegated to these platforms. As each company strives to create unique communication methods, they must also set up new safeguards against cyberbullying.
Studies show a connection between time spent online and cyberbullying tendencies. The more addicted people are to social media, the more likely they are to attack someone online.
Addressing Cyberbullying on Social Media
Thankfully, the most popular platforms include services and features that make noticing or preventing cyberbullying easier. They also all have dedicated pages for educating bystanders on the correct way to step in, whether it's physically or virtually.
Facebook (Meta)
Meta, the parent company of Facebook, created an anti- "bullying and harassment" hub. These pages teach victims, parents, and educators how to handle all types of bullying. There are even scripts that can help people practice how to respond to cyberbullying.
Sometimes it's difficult for people, especially children, to realize they're cyberbullying someone. There's a unique lack of context, tone, and emotional response when interacting with someone online.
Some resources attempt to teach people what's harmful online. If these resources don't get through, then Meta recommends blocking the attacker as soon as possible. The company also asks that bystanders flag and report the inflammatory interaction.
Instagram is another company under the Meta umbrella. The platform has strict guidelines on what's acceptable or not. However, it'd be surprising if more than 10 percent of users had read those guidelines.
Otherwise, Instagram has block and report actions to help bystanders anonymously take action against offensive posts. Influencers also can delete comments on their posts. So, there's a certain level of personal policing as well.
Twitter is a unique case when it comes to free speech and cyberbullying. Its goal is to create a safe space for all voices and ideas, with a few obvious exceptions. This policy allows for a generously drawn line between cyberbullying and candid conversations.
Unfortunately, instances of bullying can stretch for weeks without being addressed. Usually, it isn't until a user is being followed across the platform and harassed that Twitter will step in.
Like Facebook, Twitter has a "help center" section dedicated to cyberbullying, but theirs is much more focused on how users can tailor what they see. It teaches how to handle sensitive content and mute and block inflammatory comments.
TikTok
TikTok is the newest social media platform on this list. One of its most beloved features is "duet," which allows creators to splice video responses onto other people's.
This feature has led to some of TikTok's most viral videos, but it's also easily used for harassment and cyberbullying. There are many instances of "hate duets" in which a second creator will verbally, violently, or sexually harass the original poster.
It doesn't help that TikTok's algorithm rewards content with high interaction scores. So, creators feel they'll be hurt if they disable the duet feature.
TikTok's response still needs to address this problem. It debuted the "Filter All Comments" option, allowing users to search for and flag inappropriate or hateful comments. While this helps curate normal responses, it doesn't tackle the problem of hurtful response videos.
Why Does Cyberbullying Occur?
Cyberbullies strive to make their victims feel intimidated, embarrassed, and ashamed. They also do it to gain control over that individual.
Youths are more likely to engage in cyberbullying because they can’t see the power their actions have, nor do they fully understand the long-term consequences of their current actions. They cannot see the hurt expressions or pained body language of their victims. Additionally, anonymity happens to be on their side, so there are barely any consequences. Most cyberbullies are brave enough to commit these actions for this reason.
Why is it Harmful?
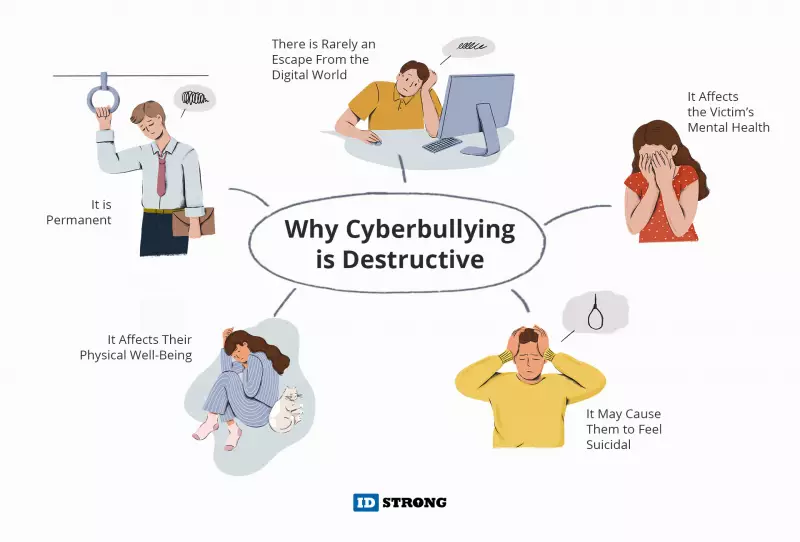
Cyberbullying can be very harmful to the victims for many reasons. The effects of cyberbullying are often adverse and long-lasting. Here are some reasons why this form of bullying is destructive:
- It is Permanent. Many employers do online background checks on their potential employees. If they find negative information - rumors, images, or videos, it lowers their chances of getting hired.
- There is Rarely an Escape From the Digital World. Many people rely on social media as a source of knowledge. Some need it to communicate with loved ones as well. Unfortunately, cyberbullies use those same platforms to harass others. So, the harassment can follow them wherever they go.
- It Affects the Victim’s Mental Health. Cyberbullying often makes the victims feel depressed, worthless, and in more severe cases - suicidal. They also tend to have lower self-esteem and self-respect.
- It Affects Their Physical Well-Being. Cyberbullying also causes adverse physical effects on victims. These include tension headaches, loss of sleep, stomach aches, and more.
- It May Cause Them to Feel Suicidal. Both victims and perpetrators are more likely to attempt suicide than those who weren’t bullied. This is why we must stand against it and know how to prevent cyberbullying.
Signs of Cyberbullying
We’ve discussed the effects of cyberbullying, but these effects aren’t noticeable. Unless the victim opens up about their feelings, nobody will know. However, key signs may help you recognize when someone is being cyberbullied. These include:
- Seeming upset or distant after using the internet or online media.
- Spending more or less time than usual online - gaming or texting.
- Having multiple email addresses, phone numbers, or texts on their digital devices.
- Being secretive about who they’re talking to and what they’re doing on social media.
How to Stop Cyberbullying
If you’re anxious about being a victim of this type of harassment, follow these tips on how to prevent cyberbullying. Similarly, if you’re a concerned educator or parent, teach your students or children to follow these safety precautions.
-
Keep Your Contact Details Private
Refrain from sharing your contact details on social media. This will prevent people you don’t know from contacting and potentially harassing you. It’s also good not to upload your email address and phone number to your social media profiles.
-
Don't Share Inappropriate Pictures and Videos
Take into consideration that most things on the internet are permanent. No matter how much you trust someone, do not share inappropriate images and videos with that person. Here’s why:
- They may end up posting that content online for everyone to see.
- They may use the content to blackmail or threaten you.
- They may be sharing that content with friends.
- Yours or their phone may get hacked, and the content you’ve shared will be in the hands of someone you don’t know.
-
Use Site-Based Settings
Play around with your settings on social media apps. Allow yourself to take advantage of your power in social media. Here are a few things you may be able to control within certain apps:
- Control who can follow you.
- Manage who will be able to see your profile.
- Set your messages or chats to self-destruct after a certain amount of time.
- Filter who can private message you.
- Limit the comments you receive or switch them off completely.
- Block or report people who make you feel uncomfortable.
-
Be Careful Who You Trust
Be skeptical of the people you interact with online. While connections feel real, it’s risky to share too much information with that person. You have no idea if that person is who they say they are or if they’re alone.
-
Keep Your Online Information Protected
When using digital accounts on public computers, make sure you log out of them when you finish. Someone else might go through your account and find your private information if left signed in.
This will create an opportunity for them to blackmail or threaten you. Alternatively, they could share the information without doing the actions above. This is usually done to be funny or mischievous.
Moreover, you must not share passwords with anyone, even if they’re someone you trust. Ensure that you have a passcode for your phone as well. This way, no one can access your accounts.
-
Don't Respond to Mean People
Responding to mean people could lead to an array of problems. They may end up sharing your responses out of context to make you look bad. In other cases, they could be annoying you simply for their entertainment.
Cyberbullies aim to make life miserable for others. Don’t feed into this habit. Rather avoid these bullies altogether.
Eventually, they will leave you alone. Another thing you can do is report and block them. This will prevent others from dealing with the same problem.
-
Practice Internet Etiquette
Think twice about the way you talk online. Sometimes the way you type or phrase sentences can be misunderstood by others.
For example, typing in all caps may seem like you are shouting. Some of your captions or comments may even sound sarcastic.
This could cause conflict with other social media users. They may send hurtful comments to you and use harmful language. It may even lead to them spreading rumors about you.
-
Report Cyberbullying
Cyberbullying usually goes against social media’s terms of use. For this reason, you can report cyberbullies to online service providers. However, some forms of cyberbullying can be quite severe and should be reported to law enforcement. These include:
- Hate crimes and stalking.
- Child pornography or sending sexually explicit messages.
- Threats of violence.
- Taking unconsented pictures or videos of someone in their private space.
Remember to keep evidence of this behavior. Online service providers will use this to take action against the cyberbully. Evidence can include taking screenshots and recording dates and descriptions of the incidents.



















































































































