What are Computer Cookies, and What Should I Know?
Table of Contents
- By Alison OLeary
- Published: May 06, 2022
- Last Updated: Jul 12, 2023
A lot goes on behind the scenes when you’re browsing the internet on your computer or mobile device. Much of the activity comes from cookies, which is a method websites use to track your online activity.
Cookies are text files that most websites store on your browser. They cache data about your browsing activity and preferences. The browser delivers the cookie back to the website when the user revisits it, allowing the website to personalize the user's experience based on the stored information.
In total, the data is called your footprint, and the individual pieces collected are called crumbs. Every time you log on and open a browser, these cookies are activated.

How Computer Cookies Work?
There are different types of computer cookies with different purposes. All track the data you leave behind when visiting websites. The top 50 websites in the United States place an average of 64 cookies on computers, for a total of more than 3,100 potential trackers.
Many cookies simply act as bookmarks for your browsing activity that allow you to pick up where you left off on a website. They keep you from repeating menial and annoying tasks that would ruin the user experience. Imagine typing in your login credentials every time you visit Twitter. There’s a good chance you’d spend significantly less time on it than on other platforms.
This applies to other unique actions you perform on a site. This includes remembering what items were in your shopping cart, turning on safe search, or recoloring hyperlinks you have already clicked on.
These cookies also allow website administrators to offer a personalized experience that shows you content specific to you. Advertisers can tailor messages to your preferences so that you’re more likely to see and click on ads that appeal to you.
Different Types of Cookies
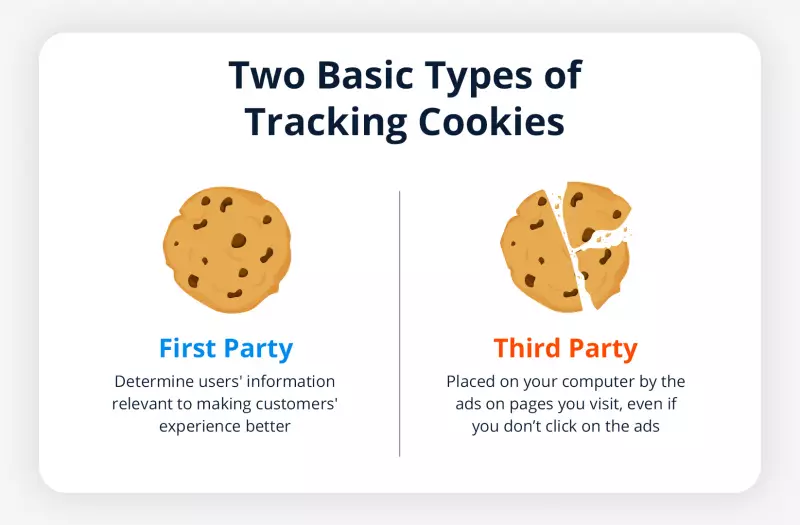
There are two basic types of tracking cookies: first party and third-party. First-party cookies are created by the website owner to improve their business. These cookies track users on the owner’s website to determine how the user found the website, the user’s location, and other information pertinent to making customers’ experiences better.
Third-party cookies are necessary for certain apps to operate for the site visitor, such as live-chat boxes. Third-party cookies are trackers put on your computer by the ads on pages you visit, even if you don’t click on the ads. Several browsers now (or soon plan to) block such cookies due to the potential to misuse the information gathered.
Other types of cookies:
- Session cookies. These follow a user only when they are on the website, then disappear and are not permanently attached to the user’s browser. They are also known as non-persistent cookies.
- Authentication cookies. These are used on subscription sites, like news and dating. These track the user during their session to confirm that the user is who they claim to be.
- Tracking cookies. These stay active indefinitely and follow users each time they visit a site.
- Zombie cookies. These are recreated versions of deleted cookies that can be difficult to locate and completely remove.
Are Computer Cookies Safe?
Cookies are plain-text combinations of letters of numbers. They aren’t programs that can deliver viruses or steal information from your hard drive. Most of the time, cookies don’t even include direct personal identifiable informations such as names, email addresses, phone numbers, or social security numbers.
However, this doesn’t mean they’re completely safe. Compute cookies can be hijacked, called session hijacking, which means that a hacker re-routes the packet of information in a cookie for his own use. Often this allows the hijacker to open a session with the user’s information stored on the cookie.
For instance, if your browser has a first-party cookie for interacting with your bank, the hijacker might be able to use that information to impersonate you on the bank’s website.
Most experts say that most first-party cookies are safe, but third-party computer cookies can be a reason for concern. These cookies continue to gather information about you across many websites. If this information is compromised, hackers have access to your personal data that should be protected. If unsecured, these computer cookies can also be stolen or manipulated by sophisticated hackers to introduce malware on your computer.
Are My Website’s Cookies Legal?
Cookie law refers to any regulations that restrict the placing of cookies on computing devices. Many people are uncomfortable with websites tracking their online activity. They view it as an invasion of privacy or a threat to their overall safety.
These aren’t unfounded fears, as some shady websites have been caught misusing or selling the information they collect through website cookies.
You must understand global cookie laws if you run an online business or any website. It can get confusing as legislation varies widely depending on your target audience and the country you’re operating in.
Below are a few countries with specific cookie laws that you should read through.
The United States of America (USA)
In the United States, cookie law is almost nonexistent. Except for a few cases, websites are allowed to track your data without notifying you of their presence.
One of the standout exceptions is the Children's Online Privacy Protection Act (COPPA). This is a federal law designed to safeguard the online privacy of children under the age of 13. The Federal Trade Commission enacted COPPA in 1998, restricting the collection of any child's personal information. Since website cookies track a user's habits, they fall under COPPA's restrictions.
COPPA only affects sites that include elements clearly targeted at children. The Commission decides this by considering the website's visual content, music, activities, and whether it leverages celebrities that appeal to a younger audience.
Thousands of websites are made daily, so COPPA places the responsibility on website operators and service providers to ensure compliance. Violations come with significant financial penalties and can even lead to permanent shutdowns.
The California Consumer Privacy Act (CCPA) is similar to COPPA, except it is for businesses targeting California consumers. The legislation focused on giving people more control over their information with the powers to:
- Know what information is collected
- Know how that information is used
- Opt out of the collection of unnecessary data
- Demand the deletion of their personal information
Under the CCPA, websites must tell users if they’re collecting cookies. This notification must also have a user-friendly opt-out button.
The European Union (EU)
The EU implemented its ePrivacy Directive in the early 2000s. The law’s contents have been revised a few times since, but it is meant to force businesses to gain the user’s consent before storing personal data in cookies. Requests for consent must be obvious, uncoerced, and withdrawable similar to the CCPA used in the USA.
The ePrivacy Directive has more than a few weaknesses. One of them is that it allows businesses to claim certain cookies as strictly necessary data for their operations. This is a vague designation that acts more like a loophole.
However, the most glaring problem came with its designation as a “Directive” rather than a “Regulation.”
In the EU, member states have a lot of freedom when choosing how to implement a directive. It simply sets a goal that all member states must reach. The degree of change varies widely, where one state does the bare minimum while another enacts sweeping online reform.
The EU proposed the ePrivacy Regulation in 2017 to address these issues. A finalized text was finished in 2021, but it’s unlikely that further discussions will happen in 2023.
Despite Brexit, the UK still adheres to most of the EU’s data privacy laws. There are a few changes in the wording, but the UK’s laws require websites to get withdrawable consent from users and share exactly how the information is used.
Canada
Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) contains ten privacy principles. One of these principles defines consent with one significant difference from other countries discussed in this post.
PIPEDA distinguishes between “express” and “implied” consent for cookies.
Express consent is the standard for most countries with cookie laws. A banner on the bottom of a website asks if you’re okay with data collection and storage.
Implied consent is when you interact with a website in a way that indicates you want to share information with it. Actions like purchasing a product or signing up for a newsletter can satisfy the requirements for implied consent. This option is vague and dangerous to rely on. We recommend always seeking express consent.
How to Clear Computer Cookies On a Browser?
Most computer security experts suggest clearing temporary internet files periodically to prevent a buildup of tracking cookies. They specifically warn about “sketchy” websites that are likely to deposit several cookies on your browser, eventually slowing down browser activity.
Some claim that blocking all cookies detracts from the browsing experience and will eventually lead to more companies using paywalls to make their websites profitable.
To clear cookies from your computer, just go to your browser’s Privacy and Security tools and click on “clear data” to delete cookies. Most sites are similar, allowing you to search for cookie settings and turn them off. Note that doing so will require you to log in to all of your protected web accounts with passwords.
A handful of browsers are popular because they block tracking cookies and protect more of your information. Some of the ways to limit or prohibit cookies include:
- Use the Duck Duck Go search engine. This option is a fan favorite for mobile users as it never logs your queries and is the default search engine for the infamous Tor browser. It loses points for not being a full browser itself, but it’s also compatible with Chrome and Firefox if you want to continue using what you already have.
- Download a Virtual Private Network (VPN) that disables tracking. Most VPNs don’t offer this service, so make sure to check for it before you check out.
- Google Chrome. Plans to reduce or prohibit third-party cookies on Chrome have been delayed significantly as Google works with clients to determine how to make the switch.
- Add a blocker like Ghostery, Privacy Badger, or uBlock Origin to Chrome.
- Brave is a new browser that promises more privacy by blocking third-party cookies by default but still allows users to interact with websites – anonymously.
- Mozilla Firefox blocks third-party cookies and crypto miners by default.
In an alarming example of misuse of personal data collected by websites, Facebook allowed a company called Cambridge Analytica to collect information on Facebook users before the 2016 presidential election in the U.S. Some of that data was collected in ways that violated Facebook’s policies. Still, Cambridge Analytica continued to use it to build profiles of users so they could create ads specifically targeted to them. The information accessed with permission from 270,000 users also gave permission to access information on their friends, which spread the impact to 87 million people.
Additional Links
https://www.ftc.gov/legal-library/browse/rules/childrens-online-privacy-protection-rule-coppa

























